The value of generative AI lies in its integration into business applications. Ultimately, AI experimentation must lead to production deployment. The big difference in security is that production deployment vastly increases the attack surface and criticality of the AI application. Production applications are connected to and deployed near production data and servers, scaled to accommodate a larger number of users, and equipped with significant computational power, all while being delivered to those users, often over the Internet. This combination requires far more careful security management than a developer’s workstation running a single copy of the AI application.
Distributed Production
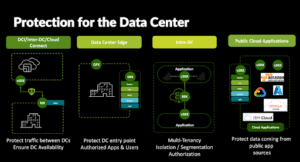
The distributed nature of most enterprises leads to distributed computing, where data is generated and processed at multiple, network-connected locations. Applications draw from numerous distributed data sources to deliver business value. Site-to-site connectivity has been shifting from dedicated private links to more VPNs over more cost-effective public links, such as the Internet or a cloud network provider. IPSec VPNs enable secure transfer over public links for high-bandwidth uses, such as AI data transfer, provided your network hardware is capable of sufficient throughput. The Juniper custom ASIC is capable of 300 Gbps of IPSec throughput, a significant figure that opens up demanding use cases for cost-effective WAN links.
Dangerous AI Models
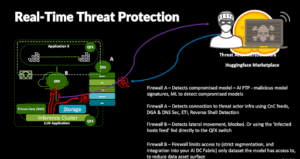
There is a fresh way for threat actors to target your network, embedding malware into AI models uploaded to public repositories like Hugging Face. An unsuspecting AI developer downloads the models and runs them on their workstation, potentially connecting the compromised model to your corporate data as part of an AI experiment. The compromised model might send your data to the threat actor, but it could also be used as a springboard to access other systems on your network. A compromised model in a development environment is undesirable; if that model reaches production, the consequences can be far more severe. The threat actor might extract production data and use the model to introduce more severe malware, such as ransomware, into your network.
A defence-in-depth strategy must start with scanning models as they enter the network, usually through a content-aware perimeter firewall. That same firewall will also defend against data exfiltration and malware that connects to command and control (CnC) servers for further instructions. Protecting the perimeter is a start, then within your network, a firewall that inspects traffic between servers should detect and prevent unusual lateral movement, which is a compromised model attempting to attack or infect another server. Even a “safe” AI model can be manipulated to return unexpected data. AI application guardrails and a content-aware firewall also help detect AI prompt injection attacks and data exfiltration. Juniper’s AI network design utilizes intelligent firewalls as the security boundary between different zones of trust, spanning from the Internet to your server and storage networks, and extending to the GPU data network.
AI DDoS Protection
DDoS attacks continue to grow in scope and size, and AI applications provide another attack vector for DDoS: the AI servers and GPUs. An AI-enabled application delivered to users over the internet typically has an API for its AI components, often exposed as a web endpoint on the internet. A DDoS attack can send thousands of requests to that API, which then sends thousands of requests to the AI servers, resulting in overloading and slowing down responses for legitimate users. Protecting that API typically involves several layers, one of which is to ensure that API requests are associated with a real instance of the application, not just malware. Another layer is in the AI API, utilizing guardrails to ensure that only valid requests are sent to the AI servers. The network layer plays a crucial role; the same botnets that attack websites are also used to DDoS AI applications, and the same techniques, such as threat feeds, IP address block lists, and rate limits, are beneficial.
Juniper Capabilities
Security must always be at the forefront of any application, network, and data center design. AI applications add some additional complexity, unique attack vectors, and new data locations. Production deployment of AI applications should not be held up by security concerns; the infrastructure and application must be built for security from the start. Juniper Networks has both products that can fulfil the connectivity and security requirements, and reference architectures for how to deploy these products in an AI data center.